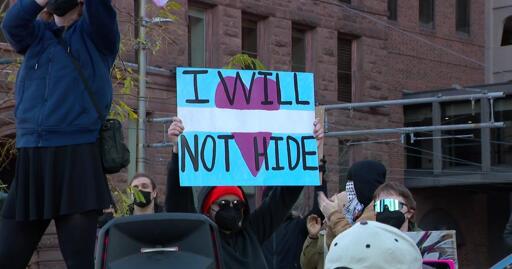The community came together Sunday to support two transgender women who say they were attacked near a light rail station in Minneapolis.
The incident happened Nov. 10 at Hennepin Avenue and Fifth Street in downtown Minneapolis. It’s where community members gathered for a rally Sunday afternoon, one week since the attack.
Amber Muhm, a community leader with Trans Movement for Liberation, said the two trans women were attacked by a group of men at the light rail station after one of the men used transphobic slurs.
“No one came to help them. In fact, they said people were cheering the attackers on while they were getting beaten,” Muhm said.
deleted by creator
Well sure, they’ve been shown that bad actions like this have the capacity to make them president of the States
deleted by creator
It’ll probably go up 80% in his 3rd term
It’ll go down to zero because these things won’t legally be hate crimes by then.
We’ve got four more years of these bigots being emboldened. I expect that these sorts of attacks are going to become a lot more commonplace, and for there to be little-to-no repercussions. Start arming yourselves.
We’ve got four more years of …
I see this all over Lemmy. Do people still not realize what has happened? The next 4 years is just the beginning of what has been unleashed for the US for at least a generation or more.
At this point, I’m choosing to believe that people are being willfully ignorant. The idea that these Nazis are going to hand power back willingly is a sick joke.
All the more reason it’s important to fight back now.
Good point. Could just be force of habit.
Everyone should have pepper spray. You can open carry a knife for defense if you like. These can both be done immediately, now, cheaply, without paperwork.
*Depending on local laws. Please check.
*depending on skin color. Please check yourself.
Like how many people were shot dead because they had a pocket knife in their hand.
In all 50 states and Washington D.C., it is legal to use pepper spray for self-defense purposes.
Age restrictions, size of containers, where you can carry it, formulations, criminal history, etc, can all be factors for pepper spray.
For knives, the size of the blade, mechanical operation, age, etc are all factors.
My comment applies. PLEASE, CHECK YOUR LOCAL LAWS.
it’s against the law in Illinois.
Don’t carry a knife unless you know how to use it in close quarters. Otherwise you’re just giving someone a knife to use against you.
Chemical deterrents are probably the better way to go, especially if you practice with it, ie know the arc distance and how to aim.
Buckle up folks, and be sure to stand up for any trans folk you know or see. It’s gonna be a rough couple of years for the trans community.
And be sure to encourage those in your life to empathize with us. Bigots are attempting to dehumanize and other us, to make us into monsters and freaks, when someone understands us as just people, neighbors, friends, family… then the virulent hate becomes seen as shameful. It disemboldens them
I’m not trans, and am fairly fem-presenting, but I’ve been accused of being a man several times since this whole bigotry thing really took off… mostly because I don’t perform femininity particularly well (deep natural voice, no makeup, comfortable clothes, never interested in men hitting on me and not afraid to say so), because it’s all bullshit I don’t care about.
As a result, I’ve more or less stopped going out since I live in a very red area (of an otherwise purple state)… I’m a small woman with disabilities, I’m not confident of my ability to protect myself against large bigoted men (who are thus far the only problem I’ve had).
Now that it’s further ramping up, I’ll just stay home at all times. That surely won’t have consequences. I can only imagine what trans people are dealing with with this stuff. My heart goes out to you.
Minneapolis is a transgender haven though in a state with some of the best pro trans laws on the books.
They were bold enough to do it there. They’re bold enough to do it anywhere.
This specific transit spot along with one on lake street is known to get pretty chaotic. There was another attack on a trans individual a year ago I believe at one of the lake street stops.
It doesn’t really have anything with being bold to do this in Minneapolis, this is known to be a light rail stop/intersection to avoid if possible.
Not knowing the details personally, this feels like a really important perspective to have on this.
It’s been a somewhat dangerous spot in downtown this year…
https://kstp.com/kstp-news/top-news/fight-turns-into-fatal-shooting-on-hennepin-ave-and-5th-street/
Sad that no one stepped in.
But I see your true colors
Shining through
I see your true colors
deleted by creator
That’s why I selected just those lines. It was an attempt at irony.
deleted by creator
She didn’t write the song so I’m not sure that’s true.
deleted by creator
I do agree with you on that, it’s a very meaningful song for me, and I do believe that Cyndi very well may have had her sister in mind when she recorded it.
deleted by creator
And this was in a blue city in a blue state. It’s gonna be really bad.
A very-nearly-battleground blue state with a significant number of angry redneck in the out state areas that blame MSP for all their troubles. (Like lacking the ability to read…)
In any case… yes it’s absolutely going to get ugly out there.
Arm yourselves.
FYI: In MN you have a duty to retreat if you can before you can legally defend yourself. It’s very likely these women would be in jail if they had shot their assailants after confronting them. Unfortunately in MN you can’t claim self defense after confronting someone when you could have retreated. Very sad situation all around.
After overhearing a group making derogatory remarks toward them at the station at Hennepin Avenue and Fifth Street in downtown Minneapolis, the pair “confronted” the group, which led to a “physical altercation,” Minneapolis Police told The Independent a statement.
Edit to add a link
Not really. You only have a duty to retreat if a reasonable person would feel they could do so safely.
Once an angry mob is surrounding you, you don’t have to make the attempt.
That said…. Taking up running will ALWAYS be more likely to save your ass than taking up shooting. Even more useful is learning to maintain (reasonable) situational awareness. Avoiding fights winds every time, hands down.
Right you can only retreat when it’s safe to do so, but what I’m saying is that if you’re legally carrying a firearm you can’t turn back around and confront people because if things do turn violent that will be used as evidence you were a willing participant, you didn’t retreat when you could have and instead continued the confrontation until it escalated to physical violence. FWIW I’m no expert but I have a permit to carry in MN and I feel like the instructor was very clear about this.
I am an expert in this (training security guards in use of force is a major part of my job, including use of firearms.)(I’m also working out of Minneapolis,)
If you actually manage to leave or disengage, and then return, then yes, it will be seen as you picking that fight.
But… again, there is no absolute duty to retreat- there is a duty to retreat if it is safe to do so. That last caveat carries a lot of work.
Basically running away is part of the use of force spectrum, and you’re only allowed to use reasonable force to prevent harm to yourself or others. The test is if a “reasonable person” would find it so… and the duty of retreat follows the same test.
Some things that would preclude a duty of retreat:
- you’re surrounded.
- they’re pointing a gun at you.
- physical obstructions block you.
- they’re in your face, and able to prevent retreat.
And, because it’s very important to keep in mind- situational awareness and avoiding the fight will always be the best and most effective self defense skill you can have. Followed closely by running. (And skill with a firearm is way way down the list.)
(In this situation, they were at a rally and got ambushed on an LRT station. It was probably unavoidable, and the goons probably came in from the outstate to do exactly what they did.)
Disturbing, that’s right outside Gay 90s.
Well, nevermind what I thought about Minneapolis.
We’re boned
Oh fuck
Whites only establishments, when?
Why are Yankees intolerant?